Just when you thought your 2018 TLS 1.2 headaches were over Microsoft recently sent out the following email to users of Azure and AD integration:
Update your servers to use TLS 1.2 for Azure AD Pass-through Authentication agents
You’re receiving this email because our records indicate that Azure AD Pass-through Authentication is enabled on your tenant, and one or more agents are running on a server that uses transport layer security (TLS) 1.1 or older to communicate with Azure AD. We recently included support for TLS 1.2 for Azure AD Pass-through Authentication, and we’re retiring support for TLS 1.0 and 1.1. To avoid any service interruptions, update your server to use TLS 1.2 before March 15, 2019.
Required action
Follow these instructions to update your servers to use TLS 1.2 by March 15, 2019:
1. Set these registry keys to enable TLS 1.2 on your Windows Server 2012 R2 or later: [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client] “DisabledByDefault”=dword:00000000 “Enabled”=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server] “DisabledByDefault”=dword:00000000 “Enabled”=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319] “SchUseStrongCrypto”=dword:00000001
2. Restart the server.
Luckily the fix is relatively painless though there are no hints as to how you might test that your agents are actually using TLS1.2 once the changes have been made. First and foremost you need to make make sure you are running a version of Azure AD connect that actually supports TLS 1.2. You can download the latest AzureADConnect.msi from here: https://www.microsoft.com/en-us/download/details.aspx?id=47594
There may be other ways to test which version of TLS the AD connect agent is using but the solution I found was to install Microsoft Message Analyser on the server that’s running the agent and capture the packets that contain the TLS information.
You can download Microsoft Message Analyser here:
https://www.microsoft.com/en-au/download/details.aspx?id=44226
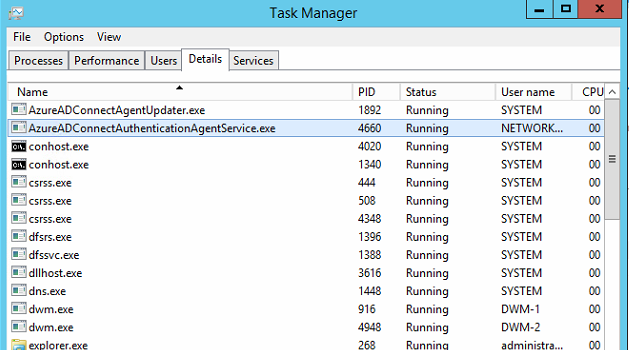
Before you start capturing packets you’ll need to get the PID of the AD connect agent service. You can do this by opening task manager and finding the process called AzureADConnectAuthenticationAgentService.exe and lookup its PID in the relevant column. You may need to add the PID column to task manager. In the below screenshot you can see that in my case the PID was 4660.
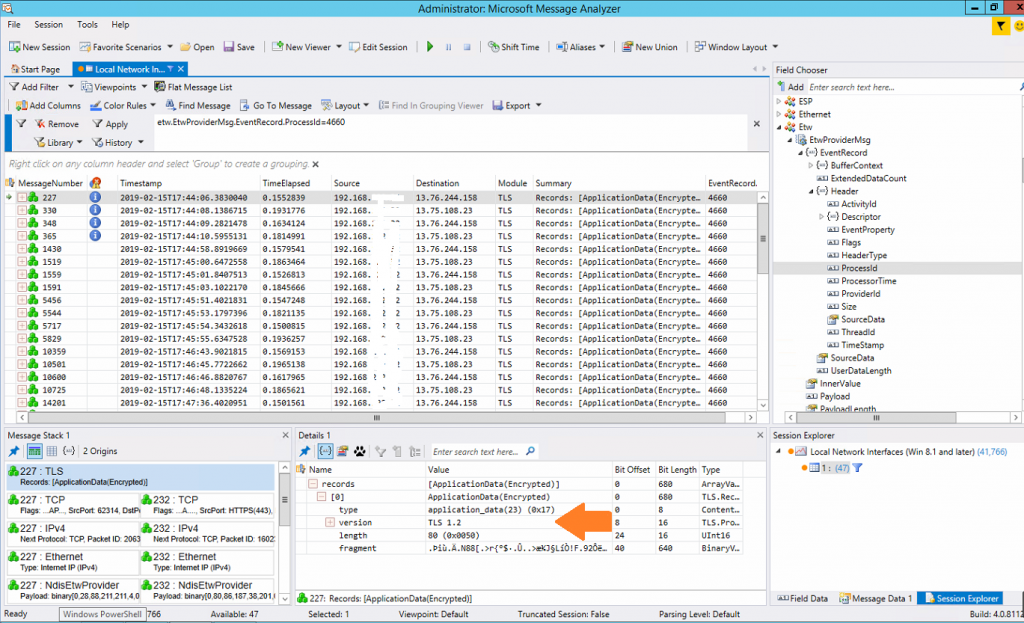
Once you have the PID start up Microsoft Message Analyser (as administrator) and click Start Local Trace, then click Add Filter and type the following line in the filter text box (replacing the PID value with your own) etw.EtwProviderMsg.EventRecord.ProcessId=4660
Finally click apply and wait for a few packets to be captured. You should eventually see something like the screenshot below. If you select one of the captured messages in the list you should see the detail panes fill with some TLS data. Hopefully youll see that magic number – TLS version 1.2 !